Discover What We Offer
Take a look at our range of services, which offers a variety of options for your business, and contact us to start working together!
Graphic Design Services
UI/UX Design
Professional UI/UX Design ensures product success via user-centric research, intuitive interactions, and visual consistency. This guide defines the de...

Brand Design
Professional Brand Design ensures market differentiation via strategic visual identity, consistency, and emotional connection. This guide defines the ...
Web Design
Professional Web Design ensures digital success via strategic user journeys, visual hierarchy, and responsive layouts. This guide defines the design p...

Digital Product Design
Professional Digital Product Design ensures long-term business viability via holistic strategy, data-driven iteration, and cross-functional alignment....
Software Development Services
Web Application Development
Professional Web Application Development builds custom software solutions that drive operational efficiency and digital transformation. This guide def...
E-commerce and Website Development
Professional E-commerce Development ensures business growth via secure transaction systems, mobile responsiveness, and scalable architecture. This gui...

Mobile App Development
Professional Mobile App Development ensures market reach via native and cross-platform solutions, seamless performance, and user engagement. This guid...

Custom Software Development
Professional Custom Software Development provides tailored digital solutions via agile methodologies, scalable architecture, and full lifecycle manage...
Desktop Software Development
Professional Desktop Software Development ensures high-performance workflows via native system integration and offline capability. This guide defines ...
Terminal (CLI) Development
Professional Terminal (CLI) Development empowers businesses through automation, precision, and server-side efficiency. This guide defines the command-...

Database Design and Development
Professional Database Design ensures data integrity via strategic schema modeling, normalization, and performance tuning. This guide defines the devel...
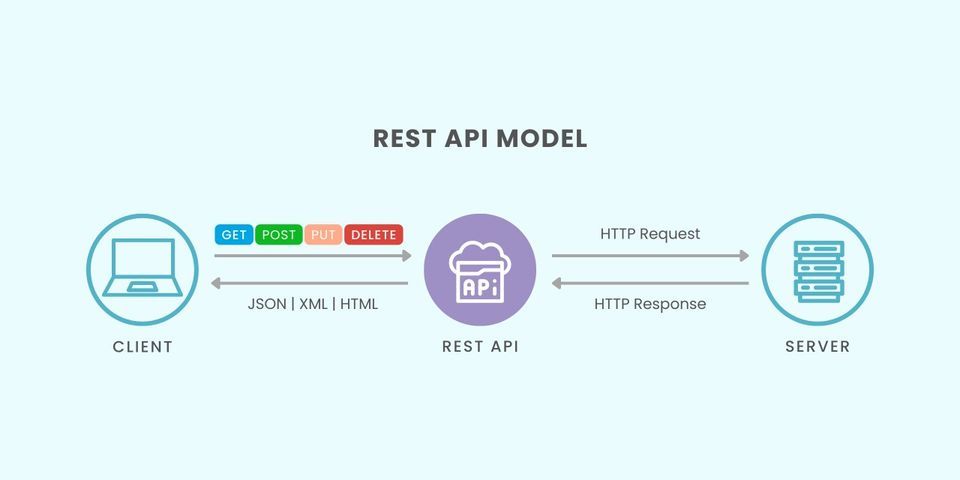
API Development and Integration
Professional API Development and Integration ensures digital scalability via strategic interface definition, robust security, and developer-centric do...
Cybersecurity Services

Cybersecurity
Cybersecurity focuses on protecting computer systems, networks, and data from cyber threats. It involves implementing measures to prevent, detect, and...

Penetration Testing
Penetration Testing, also known as ethical hacking, involves simulating cyber attacks to identify vulnerabilities in systems and applications. It help...

Data Breach Analysis
Data Breach Analysis involves investigating security incidents to determine the extent of unauthorized access or disclosure of sensitive information. ...

Data Encryption
Data Encryption involves encoding data to protect it from unauthorized access or disclosure. It uses algorithms to convert plaintext into ciphertext, ...

Virus & Malware Analysis
Virus & Malware Analysis involves studying malicious software to understand its behavior and characteristics. It helps develop countermeasures and det...

Firewall Configuration
Firewall Configuration involves setting up and managing firewall systems to control incoming and outgoing network traffic based on predetermined secur...

Network Security
Network Security focuses on securing computer networks from unauthorized access, misuse, or modification. It includes measures such as encryption, aut...

Incident Response
Incident Response involves reacting to and managing security incidents such as data breaches or cyber attacks. It includes steps such as detection, co...
System Operation Services

Data Backup & Recovery
Managed Data Backup & Recovery ensures business continuity via automated protection and immutable backups. This guide defines RPO/RTO metrics and the ...

Cloud Computing
Cloud Computing refers to the delivery of computing services such as servers, storage, databases, networking, software, and more over the Internet. It...

System Administration
System Administration involves managing and maintaining computer systems, servers, and networks to ensure their smooth and efficient operation. It inc...

Virtualization
Virtualization is the process of creating virtual instances of computing resources such as servers, storage, or networks. It allows multiple virtual m...

Containerization
Containerization is a lightweight form of virtualization that allows applications to be packaged along with their dependencies and runtime environment...

Server Management
Server Management involves overseeing the operation, maintenance, and optimization of server hardware and software. It includes tasks such as provisio...

Database Management
Database Management encompasses the administration, maintenance, and optimization of databases to ensure data integrity, availability, and performance...

Network Management
Network Management involves monitoring, controlling, and optimizing computer networks to ensure their efficient and secure operation. It includes task...

IaaS, PaaS and SaaS
IaaS (Infrastructure as a Service), PaaS (Platform as a Service), and SaaS (Software as a Service) are models of cloud computing services. IaaS provid...

Monitoring & Diagnostic
Monitoring & Diagnostic involves continuously monitoring the performance, health, and availability of IT infrastructure components. It includes real-t...
System Integration Services

IT Consulting
IT Consulting involves providing expert advice and guidance on IT-related matters to businesses. Consultants help organizations assess their technolog...

IT Strategy
IT Strategy involves developing a comprehensive plan to align technology initiatives with business objectives. It includes defining goals, assessing c...

IT Support
IT Support provides technical assistance and troubleshooting services to users or organizations experiencing IT-related issues. It includes resolving ...

Service Management
Service Management focuses on designing, implementing, and managing IT services to meet the needs of customers or organizations. It includes processes...

Business Cloud Integration
Business Cloud Integration involves integrating cloud-based services and applications into business processes and workflows. It enables organizations ...

Software Integration
Software Integration involves combining different software systems or applications to work together seamlessly. It includes integrating data, function...

Automation
Automation involves using technology to perform tasks or processes with minimal human intervention. It includes automating repetitive tasks, workflows...

User Testing
User Testing involves evaluating the usability and effectiveness of software applications or systems from the perspective of end-users. It includes ga...
